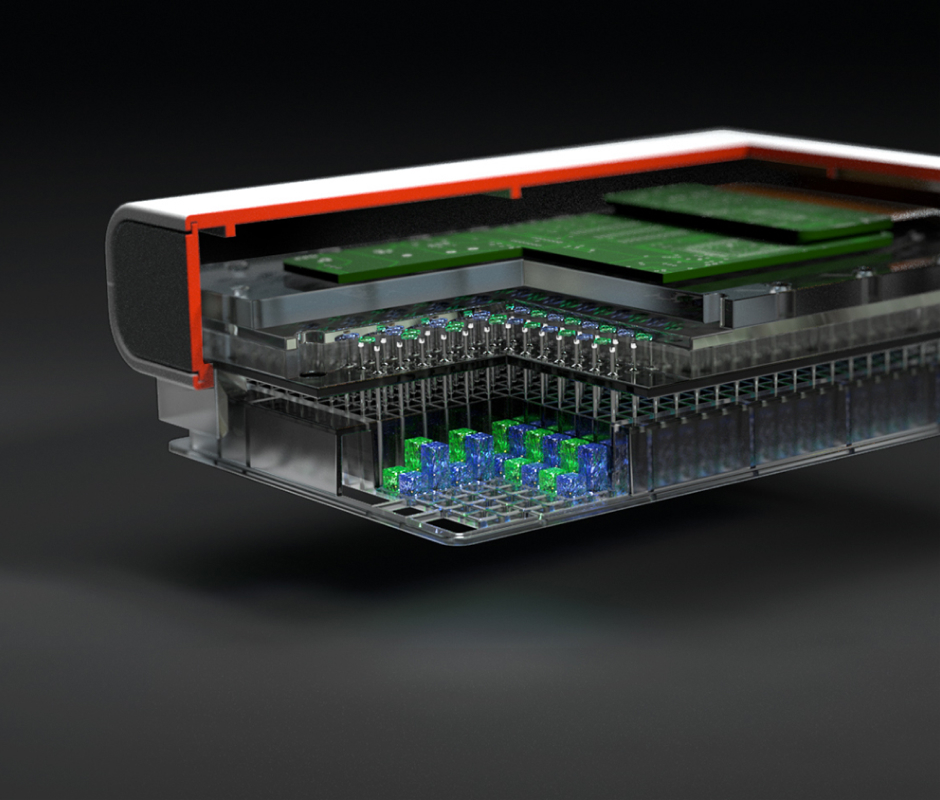
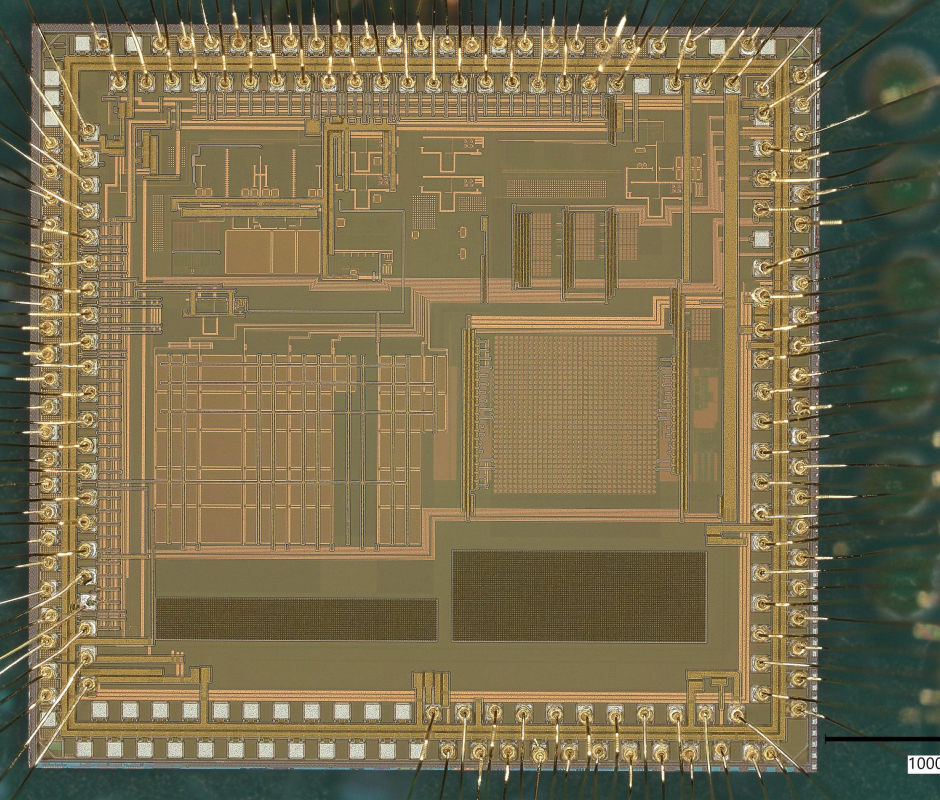
No Project is too Big or Small for Our Team
Draper excels in several market areas, showcasing expertise across diverse fields. From the vast expanse of outer space to the intricate workings of inner cells, we are at the forefront, pushing boundaries and delivering groundbreaking capabilities.
Biotechnology Systems
Engineering for Health and National Security
At Draper, we design microphysiological systems and bioprocessing technologies to expedite drug discovery and development. Our expertise extends to engineering groundbreaking medical devices, enhancing disease diagnostics and improving biothreat detection. Additionally, we lead advancements in synthetic biology to provide solutions across medical, biosecurity and manufacturing fields.
Learn More About Biotechnology SystemsElectronic Systems
Cutting-edge Technology Solutions
We recognize the dynamic nature of information technology and its accompanying threats. We are prepared to offer our customers the most advanced, precise, and dependable security solutions they require to protect our nation.
Learn More About Electronic SystemsStrategic Systems
Committed to Our Nation's Security
As part of our collaboration with the U.S. Navy and U.S. Air Force and Missile Defense Agency, we specialize in developing, testing, and delivering the world's most precise guidance, navigation and control systems. These systems include radiation-hardened electronics, precision sensors, and cyber resilience, all aimed at ensuring mission success.
Learn More About Strategic SystemsSpace Systems
Supporting the Future of Human Space Flight Since the 1950s
Our engineers develop solutions that enable space exploration, including advanced guidance, navigation and control, fault-tolerant computing, and innovative software design. Our guidance technology, which has assisted in space exploration, will continue to contribute to advancements in the final frontier.
Learn More About Space Systems